PIN pad support in Abecs protocol
In the Abecs protocol, there are guidelines so that encryption keys are no longer used to specifically capture the following bearer data:
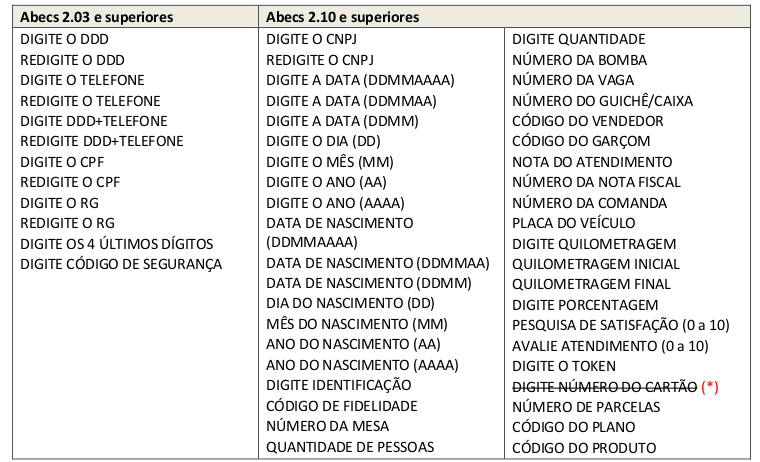
When using CliSiTef in version 7.0.115.34.rc15 (pilot version), this routine was suitable for performing a DE – TO of the collection message according to the attached PIN pad, following the algorithm:
- Ignores accents, spaces and upper/lower case differences in the carrier data capture text.
- Searches for the existence of certain strings of characters (keywords):
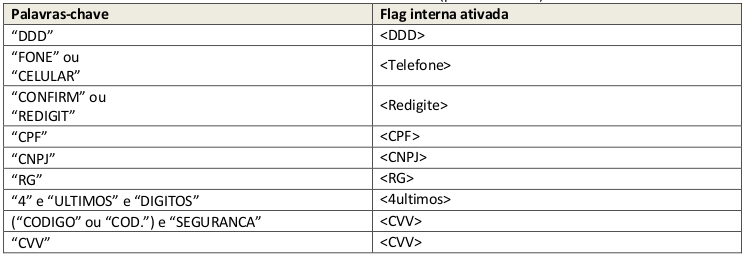
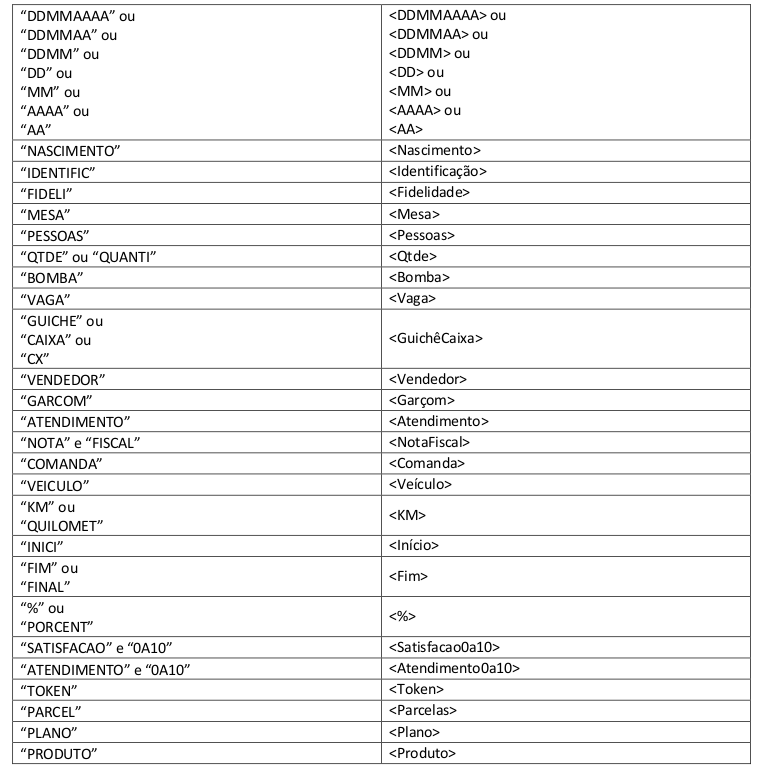
- Try to perform the final conversion according to the keywords found:
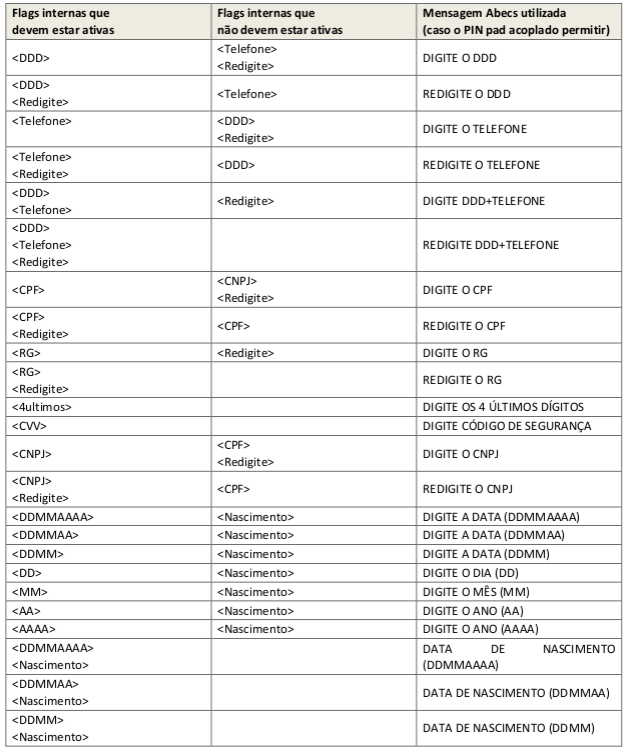
If all conversions refer to a single message code, CliSiTef will automatically make a single capture open, agglomerating the sizes, discarding all messages (the message is used fixed value defined in Table 1 - Carrier data captureable in openError! Reference source not found.) and ignoring the Access and Secret keys. Entering the PIN pad is presented without asterisks and CliSiTef does not but requests confirmation of the data on the PIN pad.
When using an open capture, the texts are fixed. It is not possible to modify these texts.
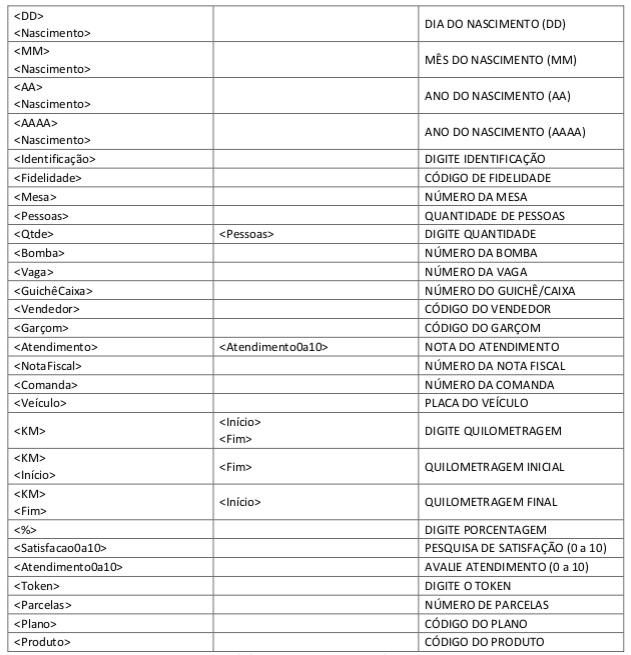
As can be seen in Table 1 - Holder data can be captured in the open, bearer data such as CNPJ, date and token can only be captured in the open from the Abecs 2.10 protocol.
If a transactional flow uses a mix of captures such as CPF + CNPJ, the CPF capture will be done open and without confirmation, while the CNPJ capture will be done encrypted and with confirmation.
It is possible that the FROM – TO conversions performed may fail for unforeseen use cases. If this occurs, please contact us.
If data cannot be collected in the open, the PIN pad encrypts the data with the DES key, which is in the obsolescence phase. This means that, in the Abecs 2.10 protocol, if CliSiTef comes across messages that do not correspond to Table 1 - Open captureable bearer data, the transaction may be aborted with code – 43 (PIN pad failure).